
Fortify Your Identity Defenses: How to Proactively Harden Your Security Posture with Rig
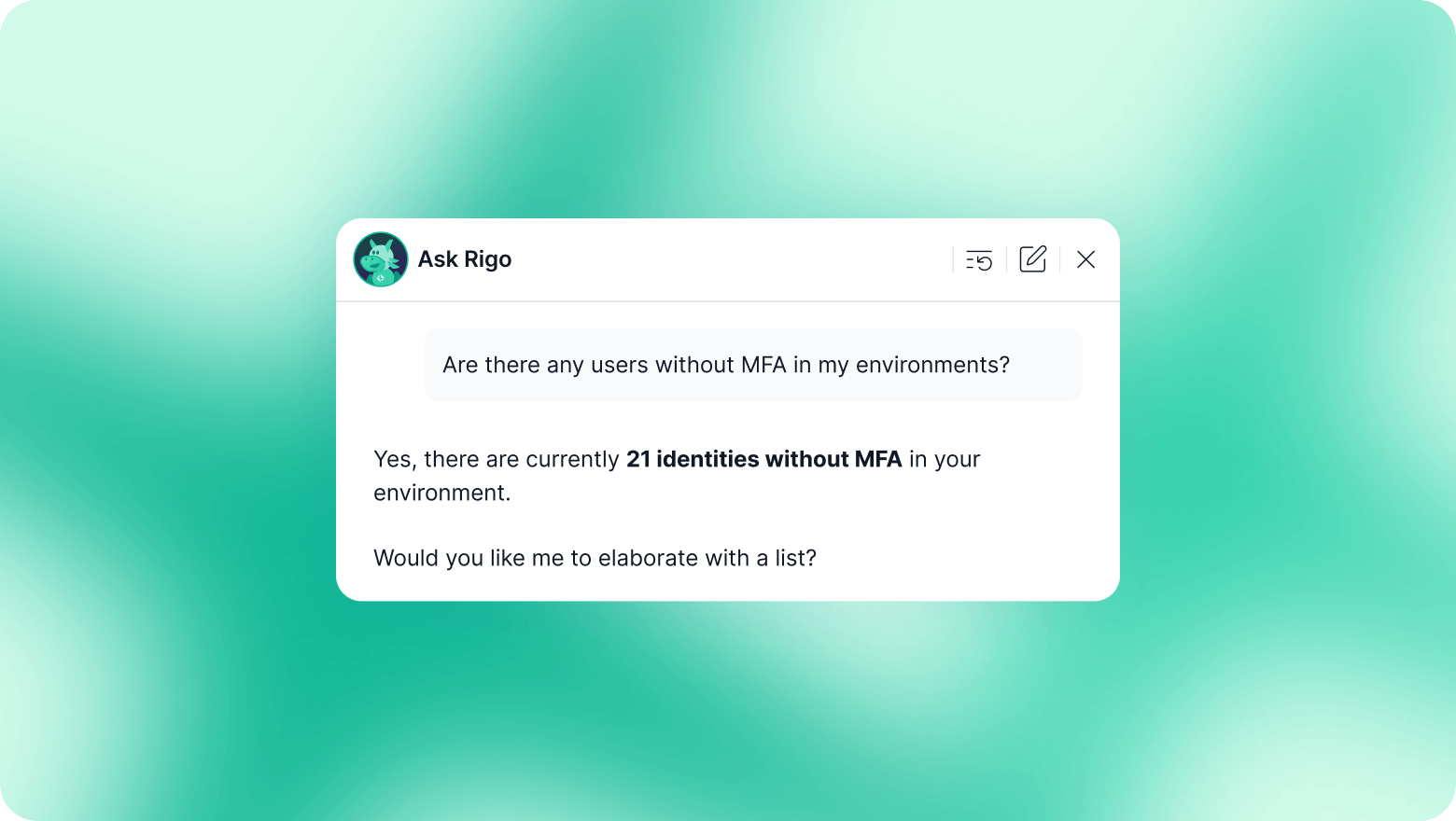
In the relentless battle against cyber threats, a reactive stance is no longer sufficient. Modern adversaries are increasingly targeting identities as their primary entry point, exploiting misconfigurations and over-privileged access long before a full-blown attack materializes. To truly secure the enterprise, organizations must shift from merely responding to threats to proactively fortifying their defenses through robust Identity Security Posture Management (ISPM).
The Critical Shift: From Reactive Cleanup to Proactive Prevention
Traditional security approaches often focus on detection and response after an attack has begun. However, identity threats frequently leverage seemingly legitimate access, making them difficult to spot once they are in motion. This highlights the urgent need for preventative controls that operate continuously, ensuring your identity infrastructure is resilient against initial compromise.
The current landscape presents several challenges that undermine a proactive security posture:
1. Incomplete Hygiene:
Many organizations struggle with basic identity hygiene, often due to a lack of continuous discovery and visibility into their vast identity landscape. This includes issues like dormant accounts, unmanaged privileged access, and clear-text credentials.
2. Misconfigurations and Excessive Privileges:
The sheer volume and complexity of cloud entitlements and permissions create a ripe environment for misconfigurations and over-privileged access. Industry data suggests that a vast majority of identities use a tiny fraction of their granted permissions, indicating widespread over-provisioning.
3. Expanding Attack Surface:
Digital transformation, cloud adoption, and remote work rapidly expand the attack surface, introducing new risks that traditional vulnerability management tools alone cannot address.
4. Siloed Tools:
Security teams often operate with a multitude of siloed tools, leading to fragmented views and hindering comprehensive posture management across the entire digital estate.
These gaps allow attackers to "log in" rather than "break in," making initial access almost indistinguishable from legitimate activity.

Rig Security: Your Foundation for Proactive Identity Fortification
Rig Security provides the essential capabilities for Identity Security Posture Management (ISPM), enabling organizations to continuously assess, manage, and improve their identity hygiene to proactively prevent identity-based attacks. By unifying fragmented identity data and providing actionable insights, Rig Security shifts your security from a reactive scramble to a strategic, preventative defense.
Here’s how Rig Security delivers proactive fortification and addresses critical posture challenges:
1. Continuous Identity Infrastructure Assessment:
Rig Security regularly evaluates the security posture of your entire identity ecosystem. This includes comprehensive management of identities across IaaS, PaaS, SaaS applications, and on-premises environments, ensuring that security controls are consistently configured and maintained.
2. Mapping User Misconfigurations and Permissions:
Rig Security provides detailed mapping of identity types, including human users (employees, contractors, vendors, and more) and non-human identities (service accounts, workload identities, API keys, and more) along with their access to resources. It highlights identity-centric misconfigurations and excessive permissions to support enforcement of the principle of least privilege
3. Context-Based Risk Assessment:
The platform goes beyond simple checklists by applying real-time, context-aware risk assessment. It analyzes posture findings alongside real-time threat signals, business context, and environment data to identify high-risk, toxic identity combinations. These are grouped into identity cases, enabling organizations to prioritize and remediate the security issues that pose the greatest risk.
4. AI-Assisted Remediation:
To simplify the remediation of reported findings and identity cases, the platform leverages an AI engine to automatically generate detailed remediation steps. These can be applied manually, semi-automatically via a downloadable script, or fully automatically.
5. "What-If" Analysis:
To help security teams and IT owners safely apply remediation steps without disrupting the business, the platform provides a “what-if” analysis feature that simulates proposed changes and visualizes their impact on the environment.
6. Unified Policy Management & Adaptive Enforcement:
Rig Security enables centralized policy creation and administration, ensuring uniformity across diverse systems. With Adaptive Policy Enforcement, access policies adjust dynamically based on contextual factors like user location, device, and behavior, even integrating with security solutions to enforce Continuous Access Evaluation Profile (CAEP) standards. This aligns with industry recommendations to adopt adaptive controls throughout the session, not just at login.
7. Streamlined Access Reviews & Identity Compliance:
Rig Security enhances the efficiency and accuracy of access certification processes through automation and risk-based prioritization. This ensures continuous compliance monitoring, facilitating audits and maintaining detailed records of access review activities.
By unifying posture findings, live signals, and contextual data into structured workflows, Rig Security empowers security teams to proactively prevent, detect, and respond to identity-related threats, securing every identity across the IT environment.
Ready to gain continuous clarity over your entire identity landscape?
Learn how Rig Security’s Unified Identity Inventory can help your organization see everything, understand risk instantly, and respond to identity-based threats effectively.
Continue reading


