Continuous Clarity: Unifying Identity Visibility Across Every Environment with Rig Security

In today's complex digital landscape, the traditional security perimeter has dissolved. Identities - both human and machine - have become the new control plane for cybersecurity, making comprehensive visibility more critical than ever. Yet, many organizations grapple with fragmented identity data, leading to blind spots that adversaries are eager to exploit. This is where a unified approach to identity visibility, powered by a platform like Rig, transforms chaos into control.
The Fragmented Reality: Why Visibility is Your Biggest Challenge
The modern enterprise is a dynamic ecosystem, spanning clouds & corporate environment, and an ever-growing number of human users, contractors, and machine identities. Each environment that manages different identity types often brings its own siloed security tools and data stores.
Industry analysts highlight that typical security operations teams often juggle an average of 50 disparate security tools, creating troublesome blind spots and delaying response times. This patchwork approach means:
1. Chained Access Blind Spots:
User actions in one system can trigger automated changes in others, creating transitive permissions that are often missed in access reviews. For example, access to a GitHub repo might indirectly affect Kubernetes via a deployment pipeline. These hidden paths obscure accountability and hinder least privilege enforcement.
2. Limited Telemetry and Analysis After the Fact:
Critical security event data is often scattered, making it difficult to get a complete picture and respond proactively.
3. Lack of Common Data Standards:
The absence of common API and data standards prevents seamless cross-communication between point solutions.
4. Poor Cross-Tool Communication:
Even with multiple tools, the lack of integration among them leaves significant gaps in overall security posture.
5. Under-Secured NHI:
While machine identities are a primary driver of identity growth and among the riskiest identity types, they are often largely under-secured and over-privileged, creating significant attack vectors. Research indicates that a large percentage of organizations (61%) still define a "privileged user" as human-only.
6. Escalating Cloud Entitlements:
Managing access entitlements in IaaS/PaaS environments is solely the organization's responsibility, and the explosion of permissions in multi-cloud environments (e.g., thousands of IAM permissions in major cloud providers) creates vast complexity.
This fragmented identity ecosystem makes it difficult to enforce least privilege, respond swiftly to threats, and ultimately creates operational drag that leaves organizations exposed to risk.

Rig Security: Your Answer to Continuous, Unified Identity Visibility
Rig Security steps in to solve these critical challenges by providing a Unified Identity Inventory that transforms fragmented identity data into a unified, actionable identity graph. As a purpose-built Identity Security Platform, Rig Security is designed to prevent, detect, and respond to identity-based threats across all environments.
Here's how Rig Security delivers continuous clarity and addresses the visibility gaps:
1. Unified Identity Inventory:
Rig Security maintains a continuously updated, comprehensive catalog of all human and non-human identities, including service accounts, API keys, cloud roles, OAuth tokens, and more. This eliminates the manual effort and ensures you always have an accurate picture of your identity landscape.
2. Visual Access Mapping:
Through graph-based visualization, Rig Security provides an intuitive way to understand complex relationships, privilege paths, and inherited permissions. This allows security and IT teams to clearly see how identities connect to resources and pinpoint where overprivileged access exists.
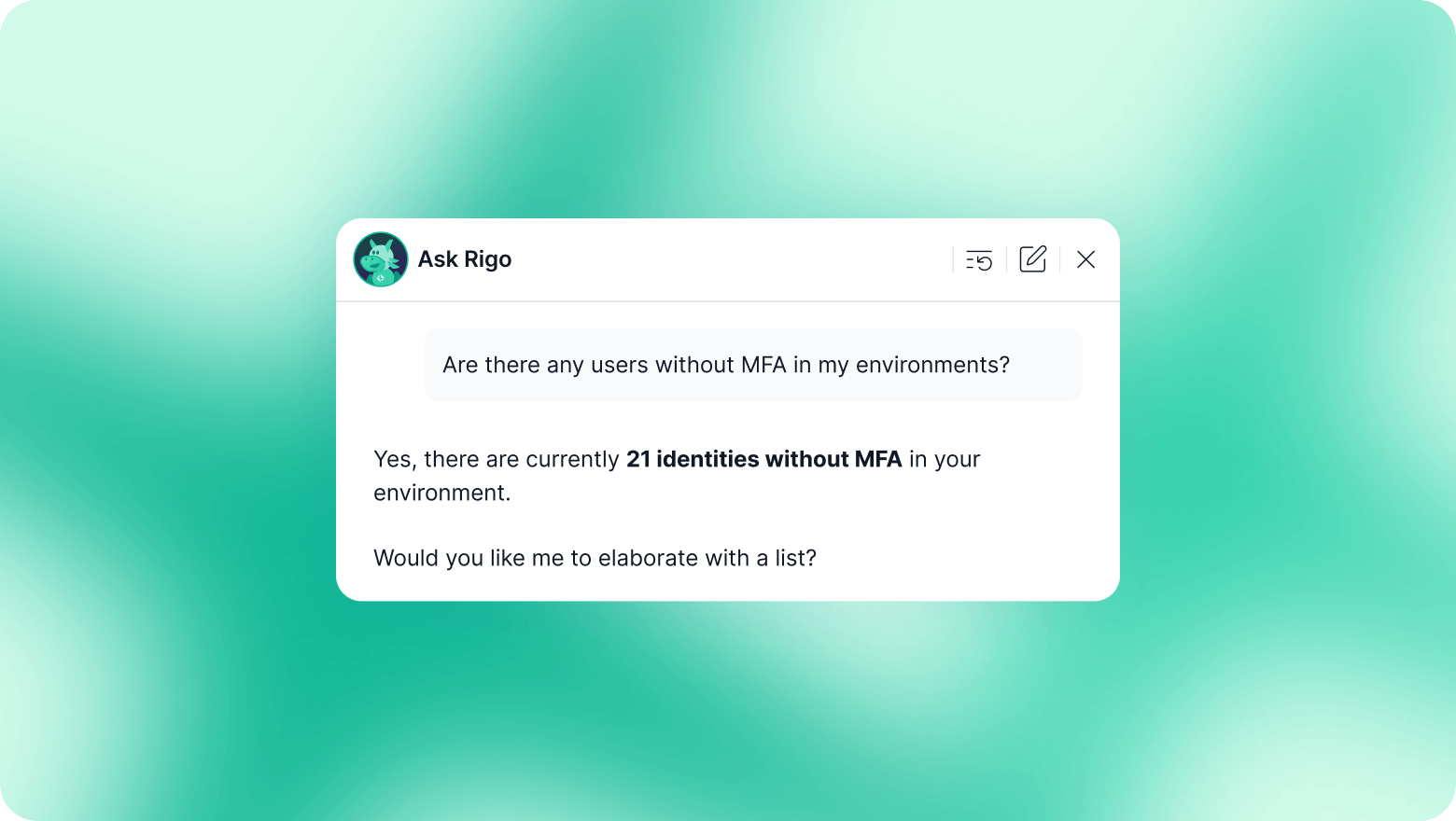
3. AI-Native Access Explorer:
Rig Security’s AI-Native Access Explorer enables instant querying of identities and permissions, allowing you to answer critical questions like "who has access to this resource?" or "which accounts have admin privileges?" with unprecedented speed and accuracy. This capability is crucial for proactive security and efficient investigations.
4. Identity Classification:
The platform categorizes identities based on type, ownership, and sensitivity. This intelligent classification supports tailored security controls, ensuring that both human and machine identities receive appropriate protection.
5. Integration with Identity Systems:
Rig Security enriches your existing IdPs and Identity processes with near real-time visibility data. This integration improves the accuracy and effectiveness of access reviews, certifications, and compliance reporting, moving beyond static snapshots to dynamic insights.
6. Coverage Across All Enterprise Environments:
Rig Security is designed to cover all enterprise environments, including cloud and hybrid setups. This comprehensive reach ensures no identity, regardless of its location, remains unmonitored or unsecured.
By consolidating identity, activity, and risk data into one unified control layer, Rig Security provides security teams with the deep, continuous visibility needed to make informed, risk-aware decisions and effectively tackle the ever-expanding attack surface. Say goodbye to fragmented views and hello to continuous clarity.
.png)
Ready to gain continuous clarity over your entire identity landscape?
Learn how Rig Security’s Unified Identity Inventory can help your organization see everything, understand risk instantly, and respond to identity-based threats effectively.
Continue reading